Are your cloud systems truly secure? Nowadays, where businesses rely heavily on these infrastructure, managing vulnerabilities has become paramount. With deployments’
increasing complexity and scale, even small security gaps can lead to significant breaches.
Cloud vulnerability management ensures your systems are protected against potential threats and breaches. However, navigating the complexities of cloud environments presents several difficulties.
In this article, we will explore these complexities and provide actionable solutions to enhance your security posture.
Complexities in Vulnerability Management
Managing vulnerabilities in these environments poses unique complexities that traditional IT infrastructures may need to encounter. Here are some key obstacles businesses face:
Complexity of Multi-Cloud Environments
A key difficulty in this aspect of management is handling multiple environments. Many organizations use multiple platforms, each with its configurations and security protocols.
Coordinating vulnerability assessments and patch management across these varied environments can be difficult.
These environments are dynamic, with assets frequently changing and scaling, complicating vulnerability scanning and assessment processes, as traditional methods may not effectively capture all instances and configurations.
Rapid Pace of Cloud Adoption
The rapid adoption of these services introduces vulnerabilities that organizations may not immediately recognize or address.
As businesses migrate more workloads to the cloud, the attack surface expands, providing more opportunities for malicious actors to exploit vulnerabilities.
Managing these vulnerabilities requires proactive monitoring and continuous assessment to keep pace with adoption rates.
Integration with Existing Security Frameworks
Integrating cloud vulnerability management tools into existing security frameworks can be complex. Security measures built for on-premises environments often don’t adapt smoothly to these platforms.
Ensuring compatibility and effective integration of vulnerability management tools with existing security systems is crucial for maintaining comprehensive protection without compromising operational efficiency.
Lack of Cloud Security Expertise
Many organizations face a shortage of skilled professionals who understand the intricacies of cloud security. Managing vulnerabilities in these environments requires specialized knowledge that differs from traditional on-premises systems.
With proper expertise, teams may be able to identify risks, configure security settings correctly, or utilize native tools effectively. This skills gap can lead to misconfigurations, leaving the systems more vulnerable to attacks.
Overcoming Complexities
Despite these complexities, effective strategies can mitigate risks and enhance security resilience:
Implementing Automated Vulnerability Scanning
Automated vulnerability scanning tools streamline the detection and assessment of vulnerabilities across these environments.
These tools continuously monitor for security gaps, providing real-time insights into potential threats.
By automating scans, organizations can proactively identify and remediate vulnerabilities before they are exploited, enhancing overall security posture.
Prioritizing Patch Management
Effective patch management is essential for mitigating vulnerabilities in cloud environments.
Establishing a prioritization framework based on risk assessment ensures that critical patches are applied promptly, reducing the window of opportunity for cyber threats.
Automated patch management solutions facilitate timely updates across multiple environments, maintaining security without disrupting operations.
Adopting a Cloud-Centric Security Strategy
Transitioning from a traditional security approach to a cloud-centric strategy is imperative for managing vulnerabilities effectively.
The native security solutions offer built-in protections and scalable defenses tailored to these environments.
By leveraging these solutions, organizations can address unique complexities associated with vulnerability management while maximizing operational efficiency.
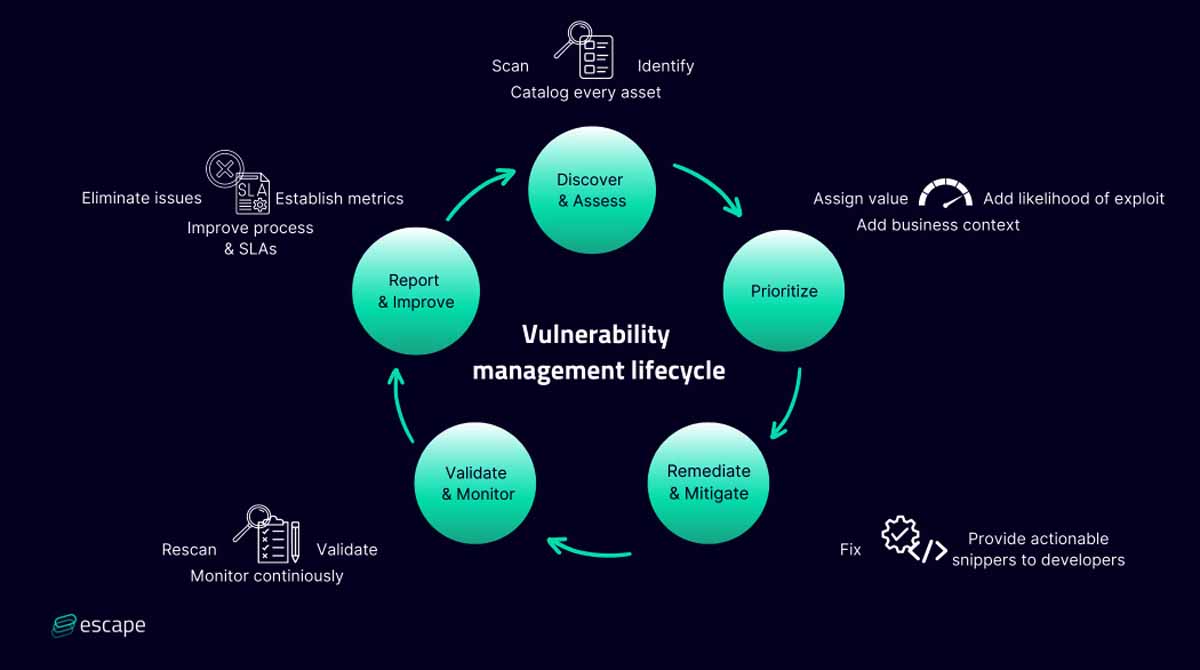
Utilizing a Management Software
Vulnerability management software is essential for identifying, assessing, and mitigating security risks across IT environments.
These tools help organizations detect vulnerabilities in their systems, applications, and networks by performing regular scans and assessments.
By providing detailed reports, they allow security teams to prioritize vulnerabilities based on their severity, ensuring that critical issues are addressed quickly.
Cloud vulnerability management is not without difficulties, but with the right strategies and tools in place, organizations can proactively protect their cloud environments from growing threats.
Embracing innovation in security practices is key to safeguarding sensitive data and maintaining trust in an increasingly digitized scope.
By staying vigilant and prioritizing security, businesses can harness the full potential of the technology while safeguarding against potential vulnerabilities.